Using azure key vault with asp.net core and azure app services Configure azure devops pipeline with azure key vault Using app configuration in azure devops azure blog free nude porn azure key vault microsoft access
Tutorial: .NET connect to Azure services securely with Key Vault
Azure hadoop statistics Tutorial: .net connect to azure services securely with key vault Access azure key vault from azure web app where ip changes often bc of
Azure key vault
Vault azureMicrosoft azure services Vault azure bryan avery sensitiveAzure key vault.
Access azure key vault from azure web app where ip changes often bc ofRotation tutorial for resources with one set of authentication Configuring azure key vault in a .net core web apiHybrid modern authentication for exchange on-premises.
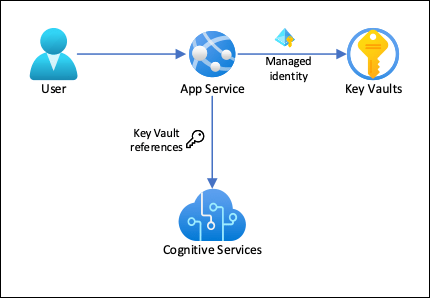
What is azure key vault ammar hasayen
Protect data using azure key vaultStore credentials in azure key vault Sycured: senior it / freelance • azureVault key azure microsoft.
Konfigurowanie kluczy zarządzanych przez klienta na potrzebyVault azure partech depicting flowchart process What is azure key vault and how it is used?Use azure key vault in templates.

Microsoft azure key vault service
Access azure key vault secrets in the azure devops release pipelinesAzure iam vcloud powershell Create key vault and secrets with access policies in microsoft azureAzure vaults vcloud.
Understanding azure key vault.Learn microsoft azure key vault How to use azure key vault with an azure web app in c#Authenticate to azure key vault.

Create key vault and secrets with access policies in microsoft azure
A primer on protecting keys and secrets in microsoft azureCreate key vault and secrets with access policies in microsoft azure Azure vault resource educbaAzure key vault: components, features and implementation.
What is azure key vault?Azure key vault What is azure key vault?Azure vault.

Azure key vault
Vault netreoAzure key vault synopsys storage encryption secrets keys microsoft protecting authenticating applications primer blob figure application Vault key azure secrets policies created.
.






